To avoid potential threats to your IT systems & database, our experts present a foolproof strategy for the security & protection of integrated systems from external attacks.
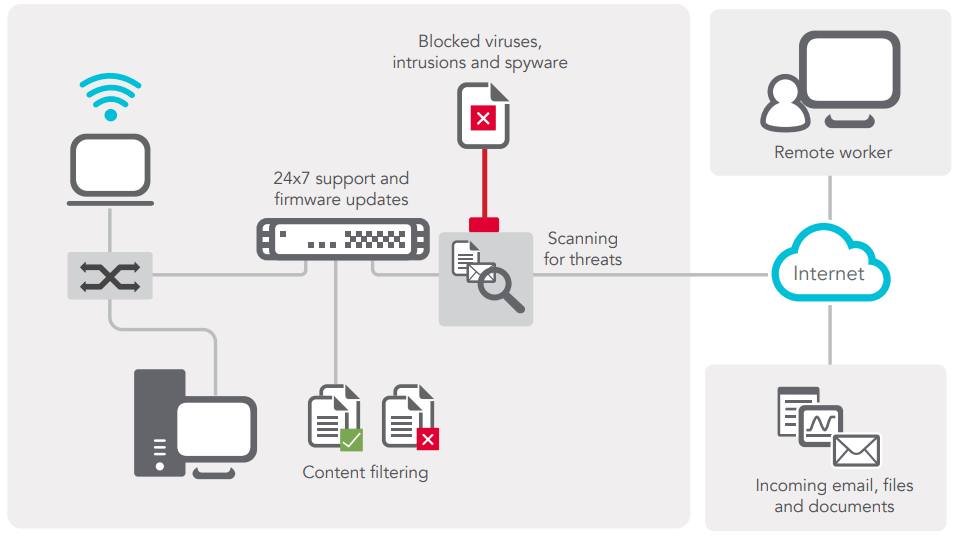
Threats to data security and company information are increasing daily. It's necessary to prevent external attacks from the Internet at many different levels. It’s also wise to protect information internally from prying eyes, and even malicious damage. In addition, contingency plans ought to be in place. These can literally save the business should a catastrophic event occur. Security equipment has advanced to cope with modern threats, but that inevitably means it become ever more complex. Without specialist knowledge, some of the tools available can be far more of an obstacle to users than a benefit.
Secure communications are possible, however (thanks to the Internet), over long distances, and cost effective too. It is possible to keep business data and communications safe and without undue restrictions on collaborative business activities. Secure Max have a great deal of experience in installing and managing security devices such as firewalls, access control devices such as key based authentication systems, as well as onsite and offsite backup and data protection systems. We are familiar with modern integrated facilities management systems too, and have design-level expertise in remote monitoring approaches. We use to ensure our clients are fully protected from external or internal threats to data security.
Network security is any activity designed to protect the usability and integrity of your network and data. It includes both hardware and software technologies. Effective network security manages access to the network. It targets a variety of threats and stops them from entering or spreading on your network. Network security is an integration of multiple layers of defenses in the network and at the network. Policies and controls are implemented by each network security layer.
Access to networks is gained by authorized users, whereas, malicious actors are indeed blocked from executing threats and exploits. Our world has presently been transformed by digitization, resulting in changes in almost all our daily activities. It is essential for all organizations to protect their networks if they aim at delivering the services demanded by employees and customers.
This eventually protects the reputation of your organization. With hackers increasing and becoming smarter day by day, the need to utilize network security tool becomes more and more impotent
A secure Web gateway is primarily used to monitor and prevent malicious traffic and data from entering, or even leaving, an organization’s network. Typically, it is implemented to secure an organization against threats originating from the Internet, websites and other Web 2.0 products services. It is generally implemented through a hardware/software gateway device application implemented at the outer boundaries of a network. Some of the features a secure Web gateway provides include URL filtering, application-level control, data leakage prevention, and virus/malware code detection.
Application security is the use of software, hardware, and procedural methods to protect applications from external threats.Once an afterthought in software design, security is becoming an increasingly important concern during development as applications become more frequently accessible over networks and are, as a result, vulnerable to a wide variety of threats. Security measures built into applications and a sound application security routine minimize the likelihood that unauthorized code will be able to manipulate applications to access, steal, modify, or delete sensitive data. Actions taken to ensure application security are sometimes called countermeasures. The most basic software countermeasure is an application firewall that limits the execution of files or the handling of data by specific installed programs. The most common hardware countermeasure is a router that can prevent the IP address of an individual computer from being directly visible on the Internet. Other countermeasures include conventional firewalls, encryption/decryption programs, anti-virus programs, spyware detection/removal programs and biometric authentication systems.
Endpoint security is designed to secure each endpoint on the network created by these devices like remote devices such as laptops or other wireless and mobile devices.Usually, endpoint security is a security system that consists of security software, located on a centrally managed and accessible server or gateway within the network, in addition to client software is installed on each of the endpoints (or devices). The server authenticates logins from the endpoints and also updates the device software when needed. While endpoint security software differs by a vendor, you can expect most software offerings to provide antivirus, antispyware, firewall and also a host intrusion prevention system (HIPS).